| Contents | |
|---|---|
 Binary Fractal Transformation Binary Fractal Transformation |
How does it work? |
 Impenetrable Guarantee Impenetrable Guarantee |
Binary Fractal Transformation cyphers cannot be penetrated |
 Unique Fractal Mapping Unique Fractal Mapping |
Your private impenetrable security zone |
 Common Fractal Mapping Common Fractal Mapping |
Used for secure Vault content transfers |
Binary Fractal Transformation
Your Vault data is secured by transforming it with an unpredictable binary fractal transformation (BFT) stream that is several times the size of your Vault data.
An unpredictable fractal portal is identified using your Vault combination.
Your combination undergoes several layers of transformation:
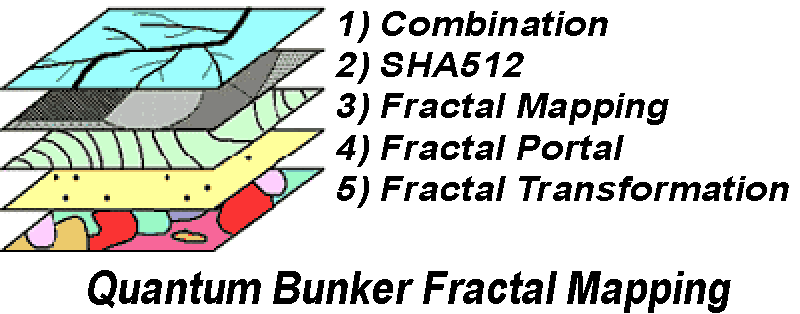
Once your combination's unique fractal portal is identified, one of an infinite number of possible fractal portals, the binary fractal transformation stream emerges using our revolutionary fractal formulas.
BFT streams are infinitely complex and unpredictable, transforming Vault data with one-way functions to the extent that the data no longer exists in the Vault data file.
There is no limit to the size of BFT streams, so they will always match and exceed the size of your Vault data.
The only way to extract your data from the Vault file is to re-assemble it with the exact BFT stream.
Impenetrable Guarantee
In contrast to common encryption that is known to be penetrable,
BFT is impenetrable. 
See our logic proof here.
While a single layer BFT is impenetrable, your Vault is transformed with multiple BFT layers:
- Personal Vault: five (5) layers
- Corporate Vault: six (6) layers
- Military Vault: seven (7) layers
Our Impenetrable Guarantee means that you can securely store your Vault file(s) on any cloud storage, company servers, laptops, PCs etc.
Without your Vault application and your Vault combination it is impossible to extract the data.
Unique Fractal Mapping
Your instance of the Quantum Bunker® application has been assembled and compiled with a unique Fractal Mapping.
Your Fractal Mapping is part of the Quantum Bunker® License.
The Fractal Mapping is unique for every owner.
The benefits of having your own unique Fractal Mapping include:
- No other Quantum Bunker® app can open your Vault file
- Only your app can open Vaults generated by your app
- Vault files can be safely stored on cloud storage
- Vault files can be shared by your app installed on different PCs
- It creates your private impenetrable security zone
The unique Fractal Mapping layer is applied to source code prior to compiling your unique Quantum Bunker® executable program.
Common Fractal Mapping
Your Quantum Bunker® application has two (2) Fractal Mappings:
- Unique Fractal Mapping: used for Vault data (see above)
- Common Fractal Mapping: used for secure Vault content transfers
The Common Fractal Mapping is the same for all Quantum Bunker® applications.
This provides a secure BFT for transferring Vault data between Quantum Bunker®s around the World.
See Secure Transfer for more details.

