
in the history of cybersecurity
We Have a Problem…
We’ve spent decades building cybersecurity around the idea that strong encryption keeps data safe. But there’s a flaw—one so fundamental that it’s been hiding in plain sight. The encryption key isn’t just protected by the system; it’s embedded within the very data it secures. And now, with the rise of quantum computing, that flaw has become an existential threat.
Quantum computers don’t break encryption the way traditional hackers do. They don’t need to guess passwords, crack algorithms, or exploit system vulnerabilities. They simply extract the key—directly from the encrypted data itself. What used to take millions of years with classical brute-force methods can now be done in real time. This isn’t hypothetical. Quantum Key Harvesting is already operational. The security infrastructure we’ve trusted—AES, RSA, ECC, key management systems, even hardware security modules—is vulnerable, not at some distant future point, but right now.
The consequences are staggering. Any encrypted data, past or present, is exposed the moment a quantum system targets it. Communications, financial transactions, intellectual property, government secrets—nothing is safe. It’s not about whether a system has been breached; it’s about the fact that the very foundations of encryption are compromised. This isn’t just a cybersecurity problem. It’s a global infrastructure crisis, and the time to act is rapidly running out.
Why Quantum Computers Can Extract Keys from Ciphers
- Quantum Computers have extraordinary properties - superposition and entanglement - quantum parallelism.
- Current Quantum Computers have sufficient qubits to crack 256 bit keys.
This means that a quantum computer can extract encryption keys in real time by testing every possible key in parallel — and finding a sensible result or reversible key much faster than any classical computer.
What would take a classical computer millions of processing years can be achieved in a single Quantum Computer cycle!
Key Takeaways:
- Quantum computers have enough qubits now to extract keys from the very ciphers they create.
- Superposition and entanglement allow quantum computers to explore all possible key combinations at the same time — undermining all cybersecurity infrastructure.
For further details see:
Quantum Key Harvesting White paper
Classic Computer Brute-Force
It takes classic computers a very long time to brute-force classic encryption because the number of distinct key combinations is very large.
To appreciate how large take a look at this table:
| Key | Comb | Decimal Combinations |
|---|---|---|
| 128 bit | 2128 | 340,282,366,920,938,463,463 ,374,607,431,768,211,456 |
| 192 bit | 2192 | 6,277,101,735,386,680,763,835 ,789,423,207,666,416,102 ,355,444,464,034,512,896 |
| 256 bit | 2256 | 115,792,089,237,316,195,423 ,570,985,008,687,907,853 ,269,984,665,640,564,039 ,457,584,007,913,129,639,936 |
These are very large numbers, and in order for a classic computer to process each combination it must 'count' through each one like an odometer and test for sensible results or key reversibility.
Encryption Decryption Asymmetry
Classic Encryption relies for its security on the fact that classic computers take a long time to test each possible combination.
It relies on 'Encryption Decryption Asymmetry', a cryptographic term that means 'fast to encrypt and slow to brute-force decrypt'.
Classic Encryption also relies on quality keys for its security. While the number of possible combinations is very large, you may be able to 'guess' a combination from password lists and other techniques.
Classic Encryption reliance on contemporary computer speed and architecture for its security means that it has always been vulnerable.
Bits v Qubits
The remarkable capability of Quantum Computers to process data simultaneously threatens Classic Cryptography.
Let's compare classic bits with quantum computer qubits:
- Classic binary computers use bits to process keys:
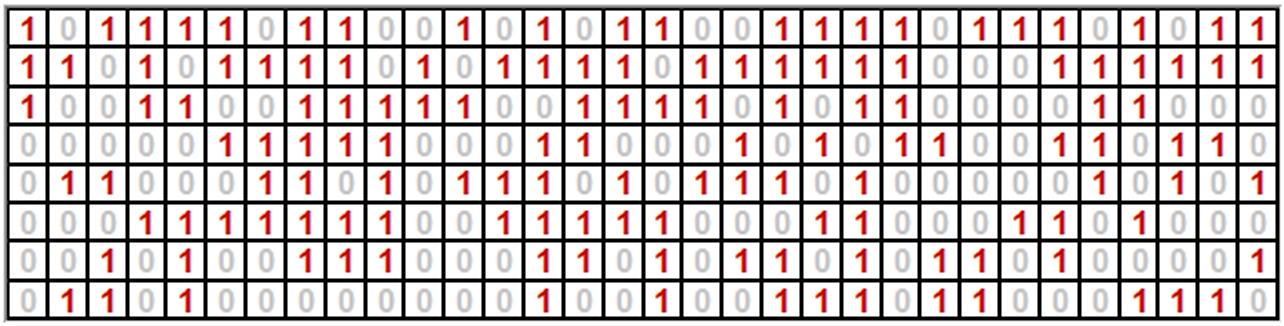
This shows 256 bits with one of 2256 possible combinations.
A classic computer must check every combination sequentially that takes thousands or millions of years.
- Quantum computers use qubits to process keys:

This shows 256 qubits processing all 2256 possible combinations simultaneously.
This is made possible by qubit entanglement and superposition.
This is the shocking reality of the quantum security threat.
AES Cracks on Today's Quantum Computers
The Flatow Algorithms turn quantum computers into AES decryption machines without needing error free qubits or years of development.
Our Quantum Security Analysts have been investigating exactly how to program a Quantum Computer to crack AES.
They are working with Artificial Intelligence (AI) ChatGPT 4o, a very competent Quantum Systems Analyst and Programmer, to research, develop and simulate these Quantum programs.
They have completed three very different Quantum Programs that all run on today's Quantum Computer, and they all prove that AES must be replaced by Quantum Proof encryption immediately.
If you are technically minded, see links to AES Quantum Cracks in resources below.
 Urgent Action
Urgent Action 
Clear and Present Danger
The time for Classic Encryption and SHA security is up...
The most urgent action for security professionals, data custodians, and organisations Word-Wide is to come to grips with the fact that:
Classic Encryption is
Quantum Toast!
Claims that "Classic Encryption is still safe if strong keys are used" and "Classic Encryption & SHA are safe until quantum computers become cryptographically relevant" are in error and have caused the quantum threat to be ignored, shelved, delayed, avoided...
Amplitude Encoded Qubits leverage single qubits to represent a whole byte by utilising the qubit capacity to compute 256 (or more) values between 0 and 1. This dramatically reduces qubit numbers while improving performance.
There is no remaining time, the danger is clear and present, our core security infrastructure is compromised and we must act to recover cybersecurity NOW.
Quantum Proof is the new Standard
All data, document and communication security that relies on Classic Encryption encryption or SHA hashing is now compromised.
Suddenly we have the biggest global cybersecurity problem in all history, estimated to affect millions of companies, billions of devices and billions of users.
This is our wake up call to global cybersecurity, your heads up to a real and present security problem that affects the entire global IT and Internet infrastructure - Classic Encryption is not Quantum Proof.
The reason this has not raised concerns before is inaccurate narratives as to the Classic Encryption/SHA quantum cybersecurity threat timeline.
The cybersecurity industry, computer and device manufacturers, operating system and software application developers suddenly have a mission-critical task; to upgrade to Quantum Proof encryption and recover lost security.
IT companies and institutions must factor significant impacts and costs to fund this mammoth upgrade.
All classic encryption and SHA functions must now be replaced by Quantum Proof FES Fractal Encryption and Fractal Hashing.
 Solutions
Solutions 
What Solutions Exist?
NIST have quantum resistant RSA replacement candidates, but no Quantum Proof replacement candidates for Classic Encryption:
It's extremely difficult to prevent quantum computers
instantaneous key cracking capabilities.
Portalz has become a world leader in Quantum Proof Cryptography for symmetric key encryption.
Over six years of fractal R&D we manifested an entirely new cryptographic art and science; Fractal Transformation (FT).
Initially considered 'an interesting encryption variation', it soon became apparent that FT is the first method of encryption that is impenetrable by any computational means - including quantum computers.
Impenetrable Encryption
is a World-First
Impenetrability is the minimum requirement in the Post Quantum Era, that's what it takes to guarantee data security, to be Quantum Proof.
Portalz has developed revolutionary new encryption technologies with unprecedented security capabilities.
A Quantum Proof Standard
Fractal Transformation is a broad and flexible security technology, with many possible parameters and algorithms.
FES is a specific selection of FT parameters and algorithms to deliver an optimum configuration proposed as the
Quantum Proof Standard
Our web contains FES details, explanations and proofs here.
For now, take it at face value that FES is indeed the worlds first impenetrable encryption and that it is the quantum proof replacement for Classic Encryption. We have not received any challenge to our published proofs.
White papers:
- Quantum Key Harvesting: White paper
- The Flatow Algorithms: Summary
- Flatow Interference Algorithm:
48 - 80 Qubit Block Encryption AES Crack - Flatow Quantum Neural Net:
118 Qubit AES Neural Net Crack - Flatow AA Algorithm:
96 - 128 Qubit AES Crack - Flatow SHA Algorithm:
352 Qubit SHA Crack
Quantum Threats:
- Quantum Key Harvesting: Cybersecurity Collapse
- AES Quantum Vulnerability: AES not Quantum Proof
- SHA Quantum Vulnerability: SHA not Quantum Proof
Quantum Proof Solutions:
- Fractal Encryption Standard: FES description
- FES Encryption Demo: live FES encryption component
- FES Hashing Demo: live FES hashing component
- Fractal Transformation: Cryptographic features
- Impenetrable Encryption: Logic and mathematical proofs
Contact:
For enquiries please contact: [email protected]