Quantum Bunker®™
Quantum Bunker® guarantees data security for your logins, keys and personal information in the post-quantum age.
Common encryption is penetrable and insecure in the quantum computer age. All existing password managers and key store methods use common encryption.
Instead of common encryption, Quantum Bunker® uses revolutionary Impenetrable Fractal Transformation to secure your vault.
Custom Military Mapping
Each Military vault is custom compiled and assembled with a unique fractal mapping for the corps, unit, force etc.
You receive a unique Quantum Bunker® vault application that ensures only your military can open your vault files. Other military will also have unique fractal mappings, so no-one else can open your vaults even if they discover your password.
Military mappings do not overlap with personal or corporate mappings, include additional features and apply more passes (default 6 passes).
Quantum Bunker® Screen-shots
Once you open your vault you can manage all your secure logins and personal information:
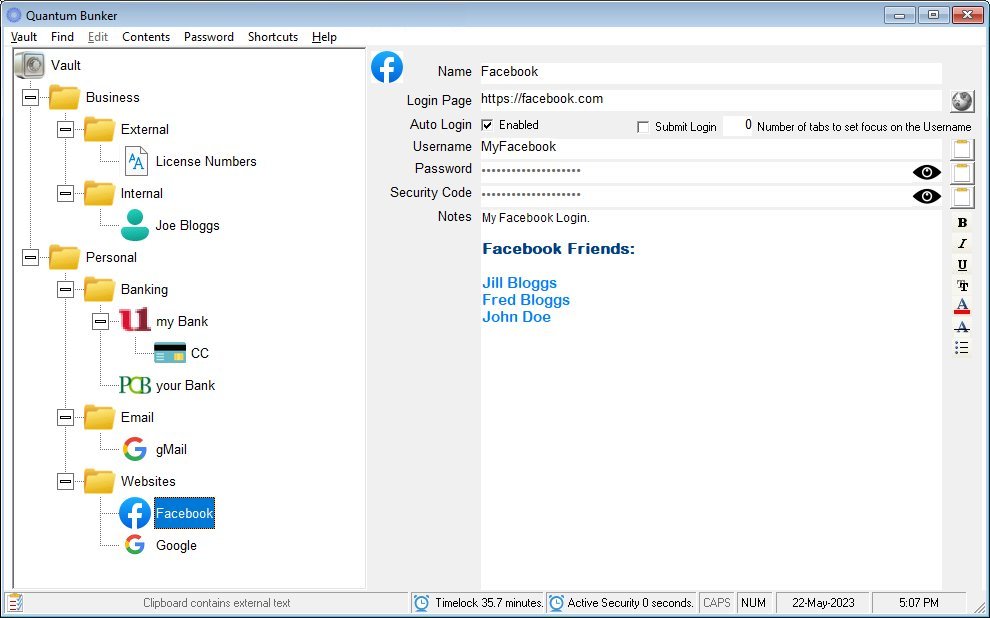
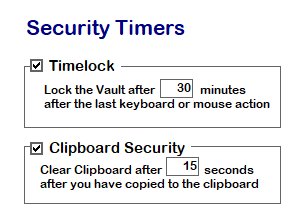
Security timers clean the clipboard after you have used it to log in, and lock the vault if it is not used:
Quantum Bunker® Features
Quantum Bunker® is the result of five years of R&D in fractal security by a team with 30 years of professional systems analyst and software development experience.
We are proud to deliver a seamless user experience, including the following features:
- Impenetrable - revolutionary quantum proof fractal data transformation
- Unique per-client - every owner receives unique secured product
- Manage multiple vaults - save different vault files for different family members
- Folder management - organise your vault with folders like windows explorer
- Navigate to Logins - one click navigation to logins with username and password
- Clipboard copy - one click to copy username or password
- Clipboard Management - clipboard cleared automatically
- Versatile Notes - format notes with bold, italics, underline, font size and color
- Contacts - securely store contact details
- Random passwords - generate secure random passwords
The military can operate their own secure cloud backup to synchronise devices.
Quantum Bunker® Benefits
The Quantum Bunker® mission is to put an end to the global explosion of cyber-attacks, hacker extortion, loss of privacy, identity, client data and money.
We know this is a big ask, but we are making a start at the top of the security pyramid - login, key and personal information storage.
Benefits include:
- Peace of mind - your Military logins, keys and secrets are secure
- Quantum security - you have secured logins and keys against quantum computer attacks
- Immunity to hackers - your keys and logins are impenetrable and secure from hackers
- Due diligence - you have met requirements for maximum login and key security
Quantum Bunker® is the security hub for a range of products planned for future release.
Military Vault
This is the Military version of Quantum Bunker® that can be installed on all of your companies devices as OS versions become available.
The OS release schedule is as follows:
- Windows - February 2024
- Android - June 2024
- Apple Mac - November 2024
- Apple IOS - December 2024
